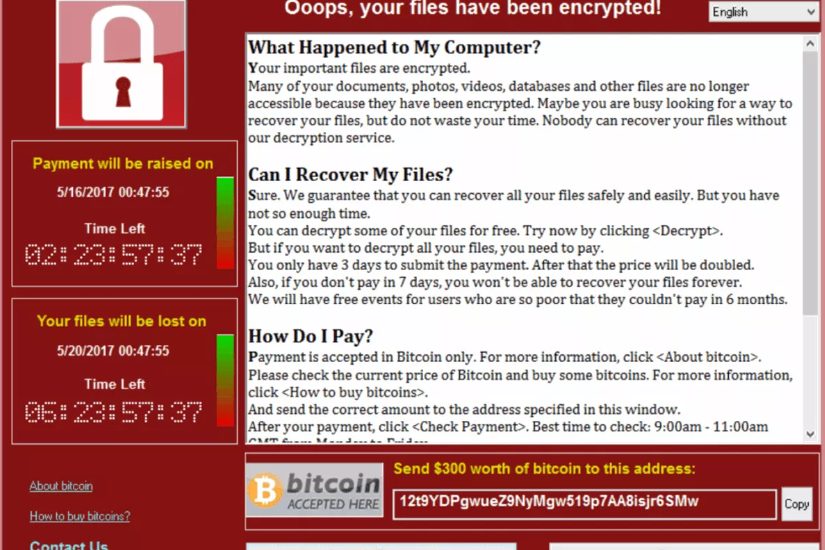
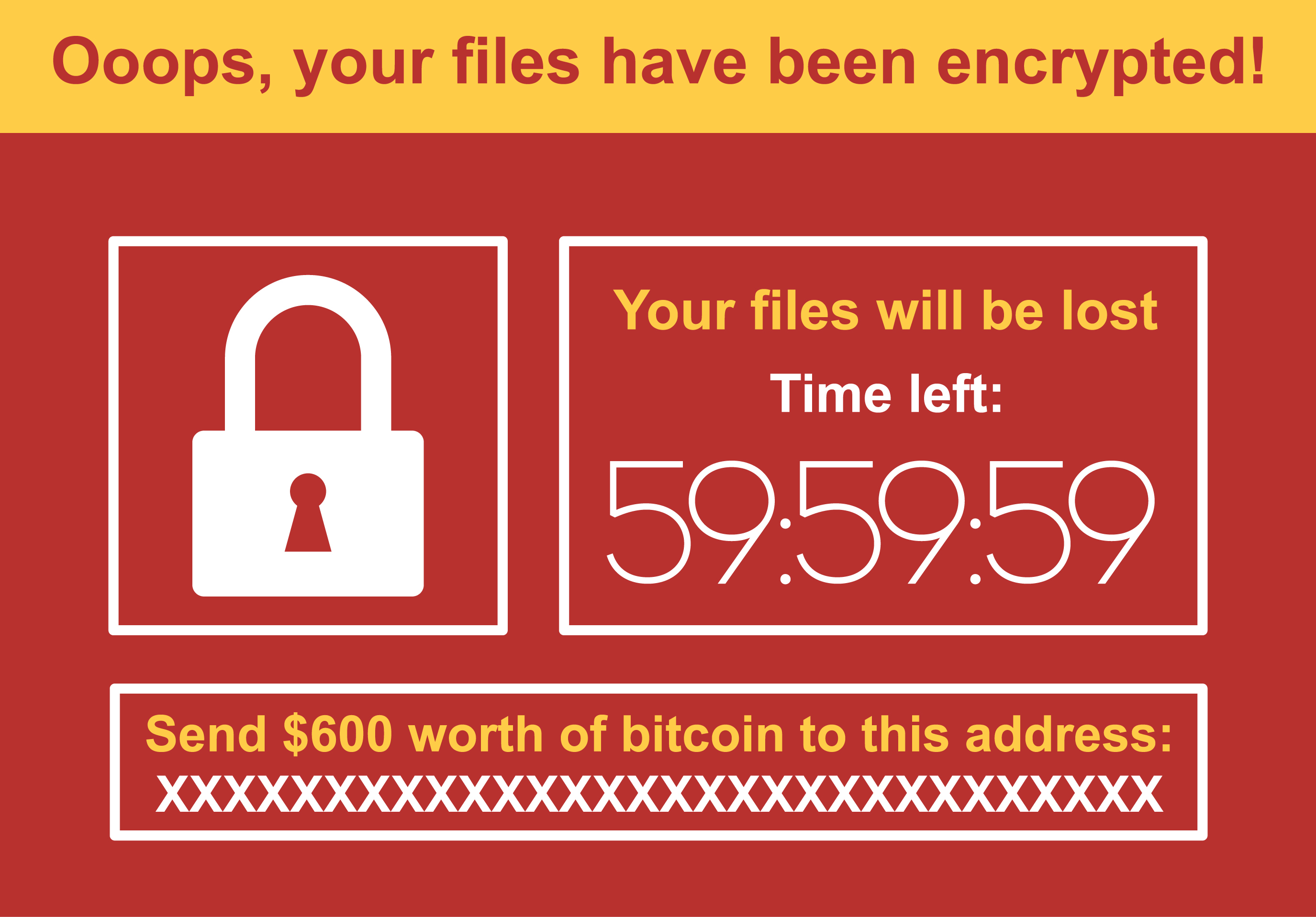
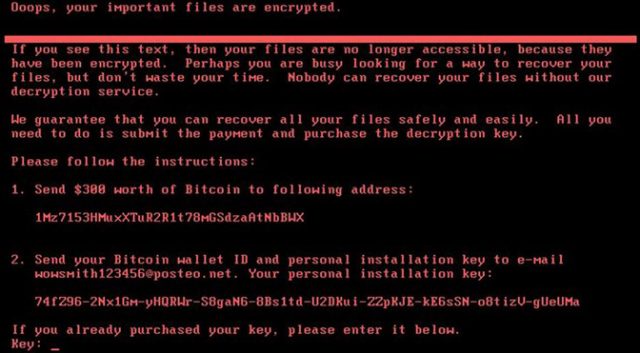
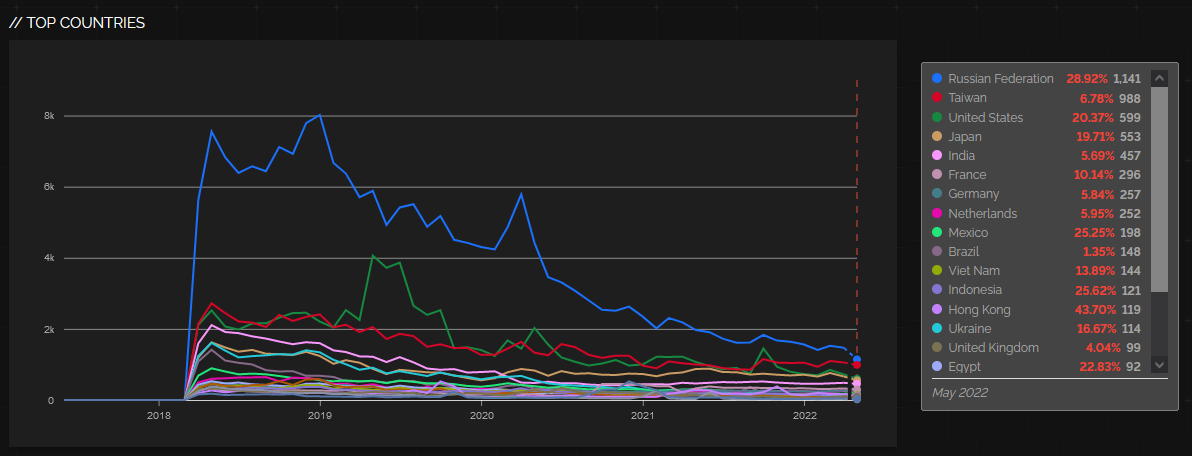
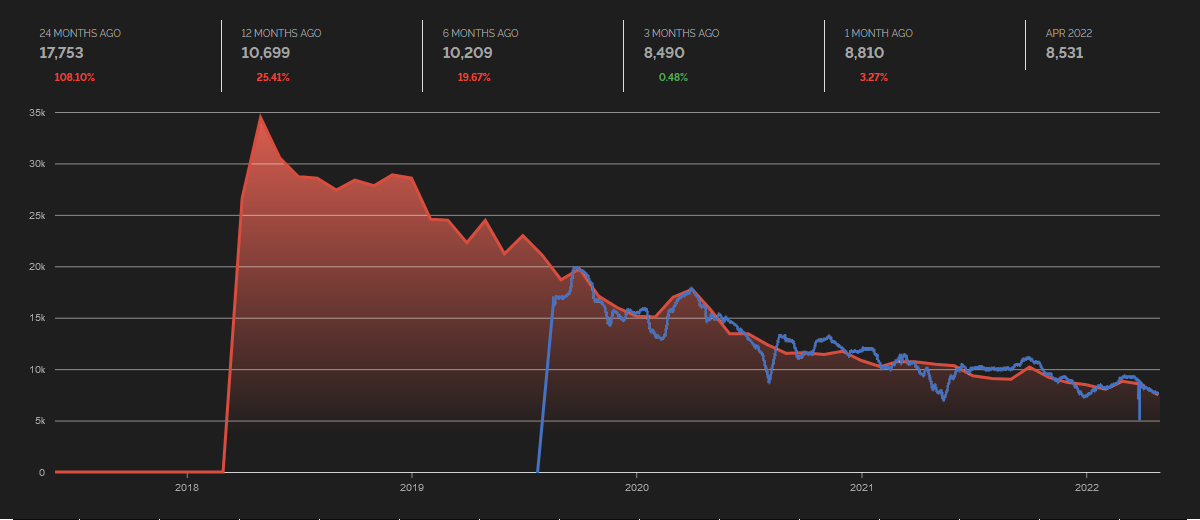
MalwareHunterTeam on X: "Progress: again being considered for deletion. See: https://t.co/1ykqnm0RLY https://t.co/SACReps7tZ" / X
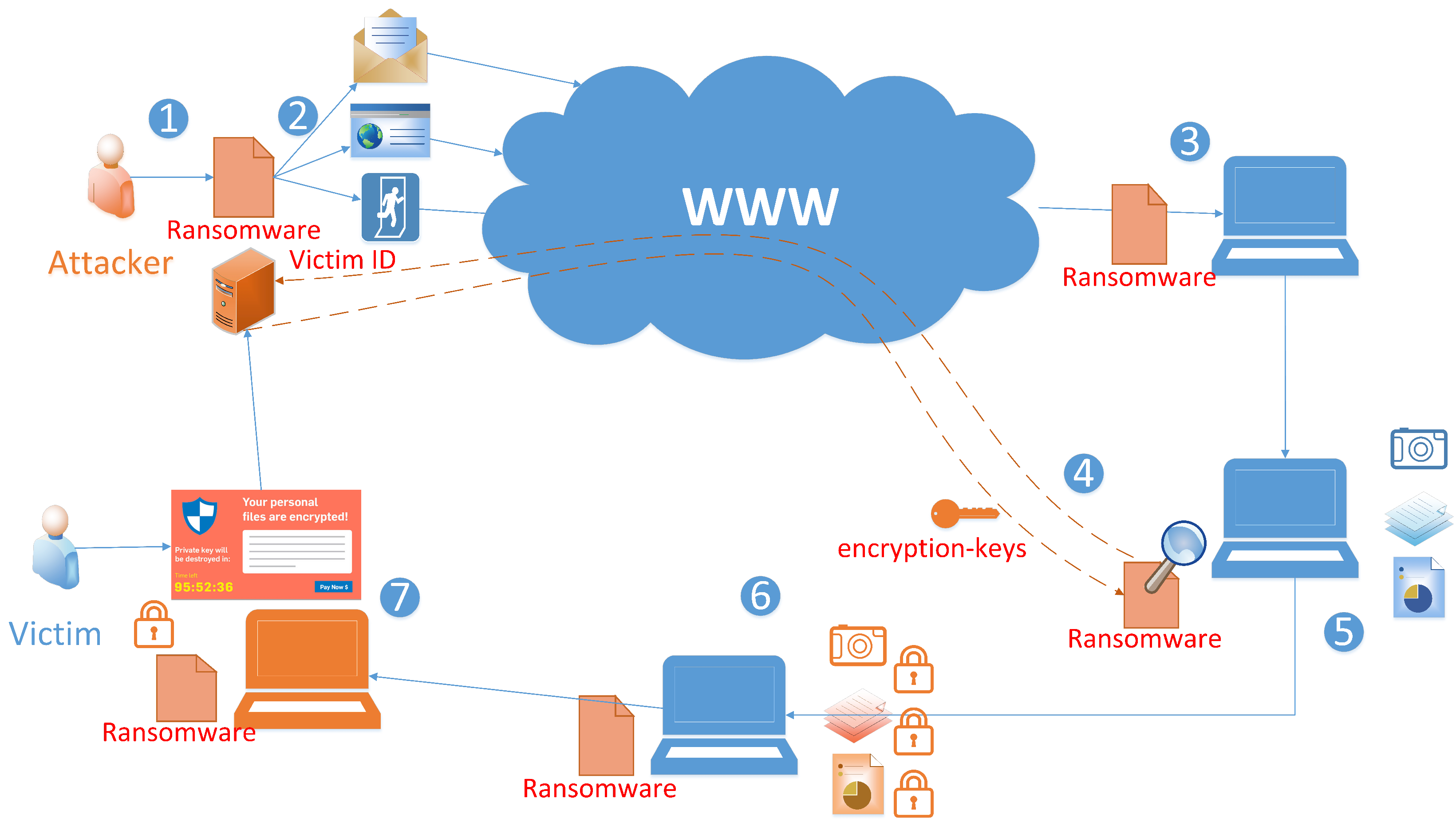
Remote Sensing | Free Full-Text | A Survey on Situational Awareness of Ransomware Attacks—Detection and Prevention Parameters

BLOG: COVID's Metamorphoses part II: A world disrupted: the consequences of the “retreat of globalisation” for nation-state cyber threats - Orpheus Cyber